FBI Gets Involved After Cryptocurrency Ransomware Attack Paralyzes Baltimore City
Tyler Durdan
About five days after Baltimore City government was paralyzed by cryptocurrency ransomware, which infected computers associated with severs tied to the city's communication network have been isolated and cleaned, reported The Baltimore Sun. But hackers are still accessing the network over the weekend, leading to a more in-depth investigation by the FBI, according to acting Mayor Jack Young.
"These people are so sophisticated that their job is just to disrupt," Young said. "I wish they would use it for more good than they are for just bad in trying to extort money from cities and companies. It's just not right."
Last Wedsenday, we were one of the first to report that hackers brought Baltimore's entire communication network to a halt.
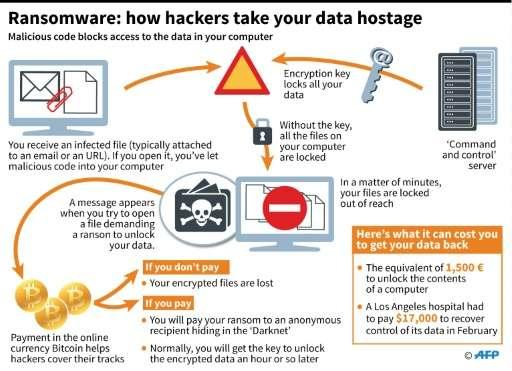
The Baltimore Sun said the ransomware was identified as RobinHood. The hackers demanded cryptocurrency as the preferred payment to unlock files on various computers.
"Everybody has been instructed to unplug the Ethernet cable and turn off power to their computers, printers and such," City Councilman Ryan Dorsey said. "It's apparently spreading computer to computer."
Hackers wrote in a note that 3 Bitcoins (equivalent to about $21,700 at current prices) would unlock each system, or approximately 13 Bitcoins (worth $86,400) to unlock the city's entire communication system.
The note also told city officials that if they contacted law enforcement that all communication would be cut off. It also emphasized that anti-virus software would damage the computers. The ransomware's procedures were entirely automated.
"We won't talk more, all we know is MONEY!" the note said. "Hurry up! Tik Tak, Tik Tak, Tik Tak!"
The FBI hasn't released any details yet, but ransomware is suspected to be behind the incident. Here's an update from the mayor on Saturday:
"No city services have been affected. People were able to get their cars at the towing yard, people come in and pay in cash or money orders or they can mail their payments in. So all the city is functioning. We're doing it a different way and the citizens of Baltimore are not being affected we just cannot get emails and those kinds of things," Young said. "We are moving forward and citizens should not notice anything other than they have to come in and do things manually."
Last week, city employees were sent home as their computers were completely inoperable.
Max Reuling, a consultant at the Baltimore City Department of Public Works and project manager at TFE Resources, said operations came to a halt last Tuesday after the ransomware attack brought down the email and critical work programs tied to Baltimore's servers. TFE Resources is a private company responsible for maintaining Baltimore's water and sewage lines. As of Saturday, he said specific communication systems were still down.
As for the ransom, Young said the hackers would get no Bitcoins.
Almost two dozen (22) local government ransomware attacks have been reported in 2019, which so far outpaces 2018.
In March, New York's state capital, Albany, was rocked with a ransomware attack.
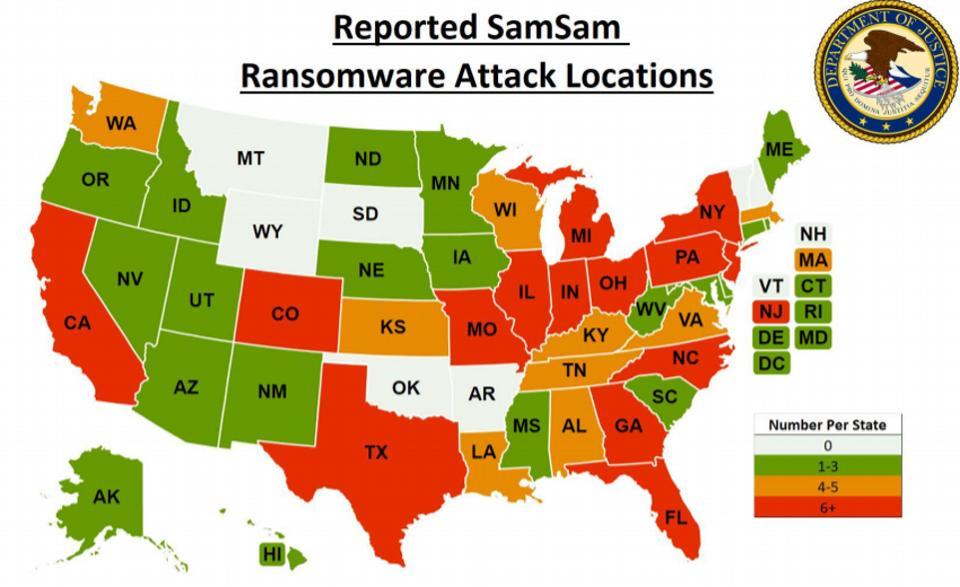
Washington has said Iran was responsible for the two most devastating ransomware attacks in the US, which took place in Atlanta and Newark last year. The ransomware, called SamSam, extorted $6 million from local governments, the Department of Justice said, and caused upwards of $30 million in damage.
WannaCry and NotPetya were the most destructive worldwide ransomware infections several years ago, were allegedly built in North Korea and Russia.
As for local governments across the US like Baltimore, they're considered 'soft targets' by America's adversaries because their networks generally aren't updated as frequently as mega-corporations.
SEE VIDEO