The Great Chinese-Iranian Stealth Reconnaissance Drone Theft Caper
by Mike Harris - Editing Jim W. Dean
The national insecurity stakes just went up once again.
Being in the armed forces of any country, at any time, has always been a hazardous occupation.
But thanks to the gross incompetence, malfeasance and short sightedness of our current and former elected officials it just became much, much, deadlier to be a US Serviceman.
This week it was revealed that a 5th generation state of the art (it does not officially exist yet) US reconnaissance drone was stolen, I mean captured, by the Iranians.
How did this happen and what is the big deal?? An unmanned drone flying at 50,000 feet invisible to radar and undetectable, so how was it stolen??
I spent my entire adult career in the technology sector, specifically the semiconductor sector, which was due to the actions that occurred during the Clinton administration while Mr. Gingrich was Speaker of the House, the semiconductor industry was off shored to China.
This industrial sector no longer manufacturers in the USA. In fact I served as a technology advisor to a certain member of the House Committee on Science and Technology.
It was during that period of time 1994-2000, that certain free trade agreements were being passed and ratified, specifically NAFTA, GATT, and membership for China within the WTO.
In conjunction with that disastrous misguided US economic policy, the military under the direction of then Vice President Al Gore was “streamlining” US Military procurement protocols.
Mr. Gore implemented a set of policies which relaxed the stringent manufacturing and testing procedures required to pass the tight Mil-Spec 883-C2 standards for all military electronic hardware and systems.
The net result was the Pentagon could continue to buy all the weapons systems they desired but with cheaper off the shelf components.
After all, they were in many instances the same part, just made to civilian standards, not manufactured to Mil-Spec, which we were assured were just as good and please consider the cost savings.
The net result was the company that I was associated with had an excuse to shut down their dedicated military use product divisions.
They could now sell off the shelf components to the military customers for use in sophisticated advanced systems, profitability goes up, and people get laid off, cost and overhead is reduced, good business, right?
So how does this ancient political history relate to the Iranian capture of a 5th generation US Spy Drone? The simple answer is: the outsourcing and off shoring of critical US technology industries.
At the time of the passage of the disastrous trade bill I cite above, the USA was #1 in the world for semiconductor production and technology, since then the USA has willingly ceded that position to China and today is not even in the top 10 semiconductor producers.
China is now the country of origin for the majority of semiconductor devices used within US Military systems. There are very few companies left who even manufacture in the USA.
How does this affect our armed servicemen and women?
We have all watched action adventure movies on TV where some young, brilliant, wonder, hacker has a back door into the super secret computer system.
Most of the time this is a software item, but if the hacker(s) are clever enough, in this case perhaps the Chinese Government itself, the backdoor can be of the hardware variety.
Very rare, impossible to detect and it must be conceived well in advance. I have direct knowledge of this type of hardware backdoor; you probably have it near you as you read this.
Anyone who has a cell phone has a system with a hardware backdoor installed. Even if the phone is powered off the FBI can turn on the device and listen to any conversation within range of the cell phone.
Your cell phone, even turned off, can also be used to locate the cell phone using embedded GPS technology. This is required for every cell phone sold within the USA.
Now that you understand the concept of the hardware backdoor, then apply this concept to the stolen stealth drone the Iranians now possess.
Given that China is now the world’s leader in producing semiconductors for US consumption, you will easily grasp the concept of how the Iranians could have seized control of the CIA’s 5th generation stealth drone and safely landed it to reverse engineer with the help of the Chinese and Russians.
In the case of the stolen CIA drone, the hardware with the backdoor was most likely embedded within he telemetry system, which is the multi-function brain of the drone, in fact every system within the drone is routed through the telemetry system, every sensor, every control, everything.
In fact the telemetry system is how the Airman at Nellis AFB uses via the joystick to fly the drone like it was a video game.
I do not know about this particular telemetry system, but from my experience at White Sands Missile Range during the early 1980’s it was common to use FM/FM modulation techniques.
All the Iranians needed was to be able to emulate one of the multitudes of frequencies used for telemetry purposes to trigger the embedded hardware purchased from the Chinese and installed within a US secret drone.
Once that hardware is triggered it is programmed to change the all the other frequencies used to control the secret drone and allow the Iranians to take total and complete control.
Imagine the young Airman with joystick in hand, and his commander at Nellis trying to capture images of any collection of buildings, gas stations, or old tires in the desert.
They might want to use these images to convince the world that the site in the photo was an Iranian nuclear weapons facility. Suddenly the Stealth drone has a mind of its own and is off mission.
“Surprise, Surprise, Surprise”, to quote Gomer Pyle. This secret spy mission to create photographic proof of Iranian nuclear intentions has gone horribly wrong.
China is the country of origin for many, many of the semiconductors used by the US Military. It was most likely that China provided the hardware with the secret backdoor that allowed the Iranians to seize control of the Stealth drone while the drone was on a secret CIA mission over Iran.
Working together, they captured a state of the art US Military stealth aircraft.
What this means to all US Military personnel serving anywhere in the world? It means that control of any electronics system in any type of platform, can be seized and used against the military that launched it.
What will happen when a fight pilot fires a missile at an enemy and it turns and blows his aircraft out of the sky?
What happens when a submarine launches a torpedo and it turns and destroys the Submarine of origin??
What happens when the AWACS systems don’t report accurate info? What happens when the Carrier Group 3C system fails??
Please take the time and apply this concept to every weapons system with electronics, they all can be turned against the USA. This event proves the entire US Military is vulnerable to being hacked.
This is Cyber Warfare at an entirely new level. Shutting down the internet won’t stop this type of cyber attack.
No electronics system within any platform is safe as long as there is any non-domestic electronics content.
Components from China are OK for a flat-screen TV, but not for critical weapons systems. Chinese components simply cannot be trusted.
Every system down to the component level must be recalled.
Any and all suspect components must be replaced, immediately before we actually place our fighting men and women in harm’s way with compromised systems.
This is an extreme threat to our National security, caused by the idiots masquerading as politicians in Washington DC.Fools and traitors have compromised the fundamentals of sound National Defense policy for a few quick bucks in their campaign coffers.
Damn them and damn the crooks and investment bankers on Wall Street who funded the de-industrialization the USA.
As a country we need certain strategic industries. In this computer age, we need a strong and vibrate semiconductor industry we cannot safely or prudently outsource this to China.
In the interim, the Pentagon should stand down all weapons systems activated since 1998, and re-activate the older, but trustworthy systems.
Until a complete and thorough recall and inspection can be conducted, any components of Chinese or foreign origin must be replaced with US manufactured devices.
This is serious people!! The very lives of our serviceman and the security of our Nation depend upon this remedial action.
—————————————-
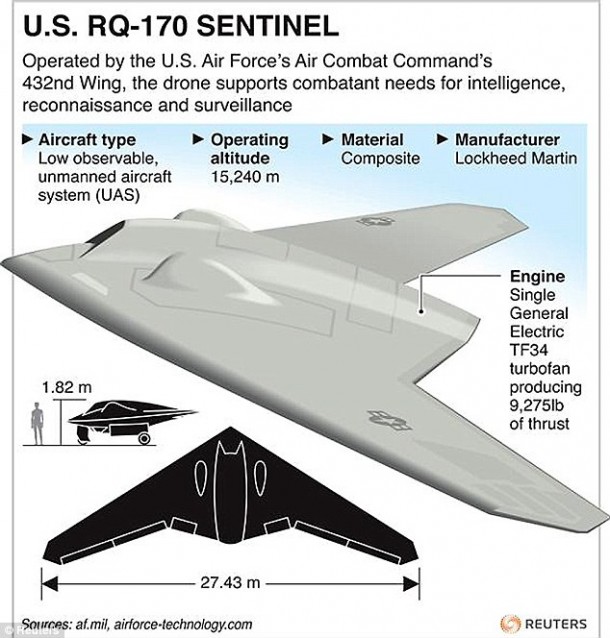
Addendum: Lockheed Martin RQ-170 Sentinel still in top secrecy
Editors Note: This article is a bit dated…as we do have a lot more photos now.The version the Iranians not have from us is the fifth generation, with the curved contours on the front edges for more radar dispersion.
Defence Aviation: Since the confirmation of the existence of the “Beast of Kandahar” by U.S. Air Force the secret is out of the stealth UAV that was seen flying out of Afghanistan in late 2007.
It was the RQ-170 Sentinel developed by Lockheed Martin’s Skunk Works as a stealth UAV and operated by the 30th Reconnaissance Squadron of United States Air Force (USAF) and has been deployed to Afghanistan as part of Operation Enduring Freedom.
There is not much record of the operational history since the UAV is kept in top secrecy and no clear photos exist as of now. RQ-170 Sentinels is known to have been deployed to Afghanistan, where one was sighted at Kandahar International Airport in late 2007.
Editors Note: We have provided you some clear photos from our sources.
In December 2009 there were also reports that the RQ-170 Sentinel had been test-flown in South Korea for the past few months and that it was expected that they would be permanently deployed in 2010 to replace Lockheed U-2 reconnaissance aircraft operating from Osan Air Base.
Again there were report in August 2010 that RQ-170s either had been or were about to be redeployed to Afghanistan and that the UAVs had been fitted with a full motion video capability.
Recently U.S. intelligence officials acknowledged that the stealthy RQ-170 Sentinel drone was indeed used to provide ISR support for the raid that killed Osama bin Laden in the Pakistani town of Abbottabad.
On the night of 1 or 2 May 2011 at least one RQ-170 monitored the area while elements of the United States Naval Special Warfare Development Group launched an assault on the compound which resulted in bin Laden’s death.
The aircraft provided footage of the attack which was watched live by President Barack Obama and his senior national security advisors.
The RQ-170 also monitored Pakistani military radio transmissions in the area to provide warning of the response to the attack.
However there was also speculation that the Sentinel’s deployments to Afghanistan and South Korea were probably undertaken to monitor Pakistan and North Korea’s ballistic missile programs.
From the low quality images of the Beast that exist aviation experts argue stealth to be moderate, the side views of the aircraft show the belly fairing which looks like it houses an electro-optical/infrared sensor at the front.
Some experts are also of the opinion that a side looking AESA (Airborne Electronically Scanned Array) radar could be housed behind it, in the belly supporting all-weather, high resolution radar-imaging by Synthetic Aperture Radar processing.
There’s still a mystery of the over-wing fairing about what is hidden beneath. Experts like Bill Sweetman of Aviation Week said:
“One possibility: they contain antennas that can be rotated, when not in use, to reduce their reflectivity, given that the best bandwidth-selective radome (radar dome) can only do so much.
So if your UAV is being illuminated by radar, you turn to place that radar on one side of the aircraft and use the antenna on the opposite, “shadow” side of the aircraft to communicate.”
The RQ-170 is estimated by Aviation Week as being approximately 66 feet in wingspan. Some expert suggests that it a wing span of about 46-90 feet with a service ceiling of about 50,000 feet and yet with an unknown engine possibly
The RQ-170 is a flying wing design and its take-off weight is estimated to be 8,500 pounds.
The design also lacks several elements common to stealth engineering, namely notched landing gear doors and sharp leading edges.
It has a curved wing platform, and the exhaust is not shielded by the wing.
Aviation Week postulates that these elements suggest the designers have avoided ‘highly sensitive technologies’ due to the near certainty of eventual operational loss inherent with a single engine design and a desire to avoid the risk of compromising leading edge technology.
It was also suggests that the medium-grey color implies a mid-altitude ceiling, unlikely to exceed 50,000 feet since a higher ceiling would normally be painted darker for best concealment.
But still many questions remain about the aircraft’s use. If it is a high-altitude aircraft it is painted an unusual color – medium grey overall, like Predator or Reaper, rather than the dark gray or overall black that provides the best concealment at very high altitudes
Since RQ-170 is a product of Lockheed Martin’s Skunk Works and property of United States Air Force nothing much can be known of it.
Experts’ claims it could be configured to carry “a high-powered microwave source” to fry computers and electronic equipment on the ground, or an electronic jamming platform to support other aircraft.
But at the official level, silence surrounds the Beast of Kandahar and its potential combat or non-combat functions.