The company named Illuminating Concepts (can’t make that up), backed by the Department of Homeland Security, has launched its new product called Intellistreets. It is street lights equipped with a speaker system, motion sensors, video cameras, mics and other crap nobody wants. Remotely controlled using Wi-Fi technology, these street lights have some interesting advantages such as energy saving and whatnot. It however doesn’t take much of an imagination to grasp to frightening police-state, oppressive potential of these lights. I mean they can film you, record your conversations, and yell orders at you while displaying a video. Anyone who has read 1984 can definitely see the frightening similarities between the “telescreens” and the hidden mics of Big Brother and this technology.
Here’s the promotional video for the product.
http://vigilantcitizen.com/latestnews/street-lights-that-spy-on-you/#comments
(4:49)
And it won’t take decades to see this street light on our streets: Intellistreets is presently being installed in Farmington Hills, Michigan.
3. New Police Pre-crime Technique - Light Based Intervention System
http://www.youtube.com/watch?feature=player_embedded&v=1punjkon-hU (3:05)


.gif)
.jpg)
(1).jpg)

.png)
 Two former high-ranking officials at the U.S. National Security Agency (NSA), a federal bureaucracy that collects data and intelligence on foreign communications for national security purposes, have come forward with allegations that the NSA actively monitors Americans as well. According to testimonies from both Thomas Drake, a former NSA senior official, and Kirk Wiebe, a former NSA senior analyst, the agency actively monitors and collects intelligence on every single American as part of a massive spying operation.
Two former high-ranking officials at the U.S. National Security Agency (NSA), a federal bureaucracy that collects data and intelligence on foreign communications for national security purposes, have come forward with allegations that the NSA actively monitors Americans as well. According to testimonies from both Thomas Drake, a former NSA senior official, and Kirk Wiebe, a former NSA senior analyst, the agency actively monitors and collects intelligence on every single American as part of a massive spying operation.

 . . . in the wake of revelations earlier in June that the National Security Agency (NSA) has been conducting blanket surveillance on Americans' electronic communications, the world's most formidable spy organization is now claiming that it has the "authority" to spy on any American, at any time, without first obtaining a search warrant.
. . . in the wake of revelations earlier in June that the National Security Agency (NSA) has been conducting blanket surveillance on Americans' electronic communications, the world's most formidable spy organization is now claiming that it has the "authority" to spy on any American, at any time, without first obtaining a search warrant.


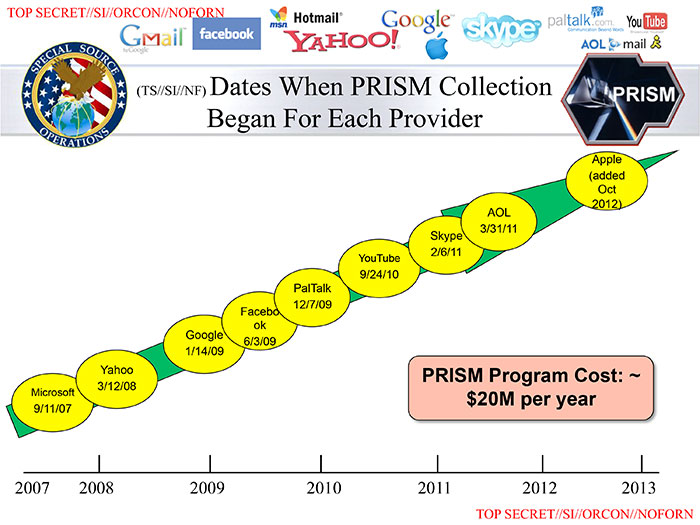
.jpg)
 I always question huge government moves. When it was announced that everyone would be pretty much forced to switch over to digital television, my antenna went up. What’s up with that? Here is what the government says:
I always question huge government moves. When it was announced that everyone would be pretty much forced to switch over to digital television, my antenna went up. What’s up with that? Here is what the government says:
 As
As  Nowhere is this more evident than in the growing surveillance society in which we live, where police are now using tens of thousands of surveillance cameras to monitor Americans everywhere they go, especially when they drive.
Nowhere is this more evident than in the growing surveillance society in which we live, where police are now using tens of thousands of surveillance cameras to monitor Americans everywhere they go, especially when they drive.
 Rates of hand washing among workers in the healthcare industry are apparently so low that some hospitals are now setting up surveillance programs to monitor the hygiene habits of doctors, nurses and other staff members. According to a recent report by the U.K.'s Daily Mail, this is precisely the method being employed by New York's North Shore University Hospital, where a complex spying system has been installed at the facility under the guise of improving cleanliness standards.
Rates of hand washing among workers in the healthcare industry are apparently so low that some hospitals are now setting up surveillance programs to monitor the hygiene habits of doctors, nurses and other staff members. According to a recent report by the U.K.'s Daily Mail, this is precisely the method being employed by New York's North Shore University Hospital, where a complex spying system has been installed at the facility under the guise of improving cleanliness standards.
 The latest blow to American health freedom came June 14 in the form of a massive 253-page proposed rule from the Centers for Medicare & Medicaid Services, a division of the Department of Health and Human Services. If approved - and there is no reason to expect it won't be - the rule "requires state, federal and local agencies as well as health insurers to swap the protected personal health information of anybody seeking to join the new health care program that will be enforced by the Internal Revenue Service," reports the Washington Examiner.
The latest blow to American health freedom came June 14 in the form of a massive 253-page proposed rule from the Centers for Medicare & Medicaid Services, a division of the Department of Health and Human Services. If approved - and there is no reason to expect it won't be - the rule "requires state, federal and local agencies as well as health insurers to swap the protected personal health information of anybody seeking to join the new health care program that will be enforced by the Internal Revenue Service," reports the Washington Examiner. 


.jpg)
.png)