
NSA Utah ‘Data Center’: Biggest-ever domestic spying lab?
From Truth
The biggest-ever data complex, to be completed in Utah in 2013, may take American citizens into a completely new reality where their emails, phone calls, online shopping lists and virtually entire lives will be stored and reviewed.
US government agencies are growing less patient with their own country with every month. First, paying with cash, shielding your laptop screen and a whole list of other commonplace habits was proclaimed to be suspicious – and if you see something you are prompted to say something. Then, reports emerged that drones are being fetched for police forces. Now, the state of Utah seems to be making way in a bid to host the largest-ever cyber shield in the history of American intelligence. Or is it a cyber-pool?
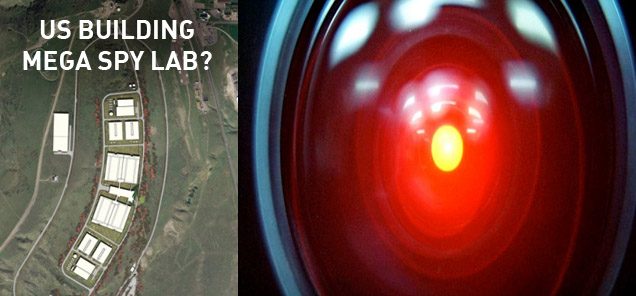
Utah sprang to media attention when the Camp Williams military base near the town of Bluffdale sprouted a vast, 240-acre construction site. American outlets say that what’s hiding under the modest plate of a Utah Data Complex is a prospective intelligence facility ordered by the National Security Agency.
Cyber-security vs. Total awareness
The NSA maintains that the data center, to be completed by September 2013, is a component of the Comprehensive National Cyber-security Initiative. The facility is to provide technical assistance to the Department of Homeland Security, collect intelligence on cyber threats and carry out cyber-security objectives, reported Reuters.
But both ordinary Americans and their intelligence community were quick to dub it “a spy center.”
The Utah Data Center will be built on a 240-acre site near Camp Williams, Utah. Once completed in September 2013, it will be twice as large as the US Capitol. The center will provide 100,000 square feet of computer space, out of a total one million square feet. The project, launched in 2010, is to cost the National Security Agency up to $2 billion.
The highly-classified project will be responsible for intercepting, storing and analyzing intelligence data as it zips through both domestic and international networks. The data may come in all forms: private e-mails, cell phone calls, Google searches – even parking lot tickets or shop purchases.
“This is more than just a data center,” an official source close to the project told the online magazine Wired.com. The source says the center will actually focus on deciphering the accumulated data, essentially code-breaking.
This means not only exposing Facebook activities or Wikipedia requests, but compromising “the invisible” Internet, or the “deepnet.” Legal and business deals, financial transactions, password-protected files and inter-governmental communications will all become vulnerable.
Once communication data is stored, a process known as data-mining will begin. Everything a person does – from traveling to buying groceries – is to be displayed on a graph, allowing the NSA to paint a detailed picture of any given individual’s life.
With this in mind, the agency now indeed looks to be “the most covert and potentially most intrusive intelligence agency ever,” as Wired.com puts it.
William Binney, NSA’s former senior mathematician-gone-whistleblower, holds his thumb and forefinger close together and tells the on-line magazine:
“We are that far from a turnkey totalitarian state.”
‘Everybody is a target’
Before the data can be stored it has to be collected. This task is already a matter of the past, as the NSA created a net of secret monitoring rooms in major US telecom facilities – a practice that was exposed by people like William Binney in 2006.
The program allowed the monitoring of millions of American phone calls and emails every day. In 2008, the Congress granted almost impecible legal immunity to telecom companies cooperating with the government on national security issues.
By this time, the NSA network has long outgrown a single room in the AT&T building in San Francisco, says Binney:
“I think there are ten to twenty of them. This is not just San Francisco; they have them in the middle of the country and also on the East Coast.”
Binney suspects the new center in Utah will simply collect all the data there is to be collected. Virtually, no one can escape the new surveillance, created in the US for the War on Terror.
Some data, of course, would be crucial in the anti-terrorism battle: exposing potential adversaries. The question is how the NSA defines who is and who is not a potential adversary.
“Everybody is a target; everybody with communication is a target,” remarks another source close to the Utah project.
Breaking the unbreakable
Now, the last hurdle in the NSA’s path seems to be the Advanced Encryption Standard cipher algorithm, which guards financial transactions, corporate mail, business deals, and diplomatic exchanges globally. It is so effective that the National Security Agency even recommended it for the US government.
Here, the Utah data complex may come in handy for two reasons. First: what cannot be broken today can be stored for tomorrow. Second: a system to break the AES should consist of a super-fast computer coupled with a vast storage capabilities to save as many instances for analysis as possible.
The data storage in Utah, with its 1 million square feet of enclosed space, is virtually bottomless, given that a terabyte can now be stored on a tiny flash drive. Wired.com argues that the US plan to break the AES is the sole reason behind the construction of the Utah Data Center.
The eavesdropping issue has been rocking the US since the Watergate scandal in the 1970s, when domestic spying was eventually outlawed. Nowadays, a lot of questions are still being asked about the secret activities of the US government and whether it could be using the Patriot Act and other national security legislation to justify potentially illegal actions. The NSA’s former employees, who decided to go public, wonder whether the agency – which is to spend up to $2 billion on the heavily fortified facility in Utah – will be able to restrict itself to eavesdropping only on international communications.#Link
New technologies are making the work of CIA Director David Petraeus a whole lot easier. According to him, the advent of wireless and web-connected devices has caused citizens to bug their own home, effectively allowing the spy agency to collect a wealth of information with great ease. If that wasn’t enough, people now readily share the most (in)significant details of their lives through Facebook, which now displays all of this information in a very convenient time-line.
Another concept that is brushed upon in this article is cloud computing. Touted as the next big thing in computer technology, cloud computing is about storing all of your data in “remote secure servers” – ultimately eliminating the need for computer hard drives and storage devices such as USB sticks. While this technology sounds very convenient, it is set to cause a drastic change in the world of computing: In just a few years, almost all of the personal files, pictures and data of computer users across the world will be stored in gigantic servers that will be owned by only a few mega-companies. Apple already has a system called iCloud that automatically copies the contents of iPhones and iPads (including pics, contacts, etc.) to a remote server. As Pertraeus himself says, all of this information is now “located, identified, monitored, and remotely controlled” by the CIA – and whoever else. Here’s an article about Petraeus love of new technologies from Wired.
CIA Chief: We’ll Spy on You Through Your Dishwasher
More and more personal and household devices are connecting to the internet, from your television to your car navigation systems to your light switches. CIA Director David Petraeus cannot wait to spy on you through them.
Earlier this month, Petraeus mused about the emergence of an “Internet of Things” — that is, wired devices — at a summit for In-Q-Tel, the CIA’s venture capital firm. “‘Transformational’ is an overused word, but I do believe it properly applies to these technologies,” Petraeus enthused, “particularly to their effect on clandestine tradecraft.”
All those new online devices are a treasure trove of data if you’re a “person of interest” to the spy community. Once upon a time, spies had to place a bug in your chandelier to hear your conversation. With the rise of the “smart home,” you’d be sending tagged, geolocated data that a spy agency can intercept in real time when you use the lighting app on your phone to adjust your living room’s ambiance.
“Items of interest will be located, identified, monitored, and remotely controlled through technologies such as radio-frequency identification, sensor networks, tiny embedded servers, and energy harvesters — all connected to the next-generation internet using abundant, low-cost, and high-power computing,” Petraeus said, “the latter now going to cloud computing, in many areas greater and greater supercomputing, and, ultimately, heading to quantum computing.”
Petraeus allowed that these household spy devices “change our notions of secrecy” and prompt a rethink of “our notions of identity and secrecy.” All of which is true — if convenient for a CIA director.
The CIA has a lot of legal restrictions against spying on American citizens. But collecting ambient geolocation data from devices is a grayer area, especially after the 2008 carve-outs to the Foreign Intelligence Surveillance Act. Hardware manufacturers, it turns out, store a trove of geolocation data; and some legislators have grown alarmed at how easy it is for the government to track you through your phone or PlayStation.
That’s not the only data exploit intriguing Petraeus. He’s interested in creating new online identities for his undercover spies — and sweeping away the “digital footprints” of agents who suddenly need to vanish.
“Proud parents document the arrival and growth of their future CIA officer in all forms of social media that the world can access for decades to come,” Petraeus observed. “Moreover, we have to figure out how to create the digital footprint for new identities for some officers.”
It’s hard to argue with that. Online cache is not a spy’s friend. But Petraeus has an inadvertent pal in Facebook.
Why? With the arrival of Timeline, Facebook made it super-easy to backdate your online history. Barack Obama, for instance, hasn’t been on Facebook since his birth in 1961. Creating new identities for CIA non-official cover operatives has arguably never been easier. Thank Zuck, spies. Thank Zuck. #Link
When people download a film from Netflix to a flatscreen, or turn on web radio, they could be alerting unwanted watchers to exactly what they are doing and where they are.
Spies will no longer have to plant bugs in your home – the rise of ‘connected’ gadgets controlled by apps will mean that people ‘bug’ their own homes, says CIA director David Petraeus.
The CIA claims it will be able to ‘read’ these devices via the internet – and perhaps even via radio waves from outside the home.

Everything from remote controls to clock radios can now be controlled via apps – and chip company ARM recently unveiled low-powered, cheaper chips which will be used in everything from fridges and ovens to doorbells.
The resultant chorus of ‘connected’ gadgets will be able to be read like a book – and even remote-controlled, according to CIA CIA Director David Petraeus, according to a recent report by Wired’s ‘Danger Room’ blog.
Petraeus says that web-connected gadgets will ‘transform’ the art of spying – allowing spies to monitor people automatically without planting bugs, breaking and entering or even donning a tuxedo to infiltrate a dinner party.
‘Transformational’ is an overused word, but I do believe it properly applies to these technologies,’ said Petraeus.
‘Particularly to their effect on clandestine tradecraft. Items of interest will be located, identified, monitored, and remotely controlled through technologies such as radio-frequency identification, sensor networks, tiny embedded servers, and energy harvesters - all connected to the next-generation internet using abundant, low-cost, and high-power computing.’
Petraeus was speaking to a venture capital firm about new technologies which aim to add processors and web connections to previously ‘dumb’ home appliances such as fridges, ovens and lighting systems.
This week, one of the world’s biggest chip companies, ARM, has unveiled a new processor built to work inside ‘connected’ white goods.
The ARM chips are smaller, lower-powered and far cheaper than previous processors – and designed to add the internet to almost every kind of electrical appliance.
It’s a concept described as the ‘internet of things’.
Futurists think that one day ‘connected’ devices will tell the internet where they are and what they are doing at all times – and will be mapped by computers as precisely as Google Maps charts the physical landscape now.
Privacy groups such as the Electronic Frontier Foundation have warned of how information such as geolocation data can be misused – but as more and more devices connect, it’s clear that opportunities for surveillance will multiply.#Link
